High-intensity cybersecurity attacks on the rise, Telia Carrier reports
Telia Carrier says that DNS and NTP amplification attacks were the most common attack vectors last year.

Telia Carrier's first DDoS Threat Landscape Report shows an increase in high-intensity cybersecurity attacks in 2020 versus 2019, and a 50% rise in peak attack traffic over that time period.
"With an increase in available network capacity overall, cyber-criminals are increasingly targeting their victims with high-intensity packet-per-second attacks, rather than simply congesting client links," Telia Carrier explained in its DDoS report.
By examining traffic data on its global Internet backbone, AS1299, Telia Carrier identified a spike in DDoS attacks in 2020; the largest attack reached 1.18 Terabytes per Second (TBPS) or 887 Mega Packets Per Second (Mpps). Telia Carrier says it cleaned 57 Petabits or 14 tera packets of malicious data in 2020, and the average size of a DDoS attack was 19 Gbps (23 Mpps), lasting an average of 10 minutes. Jorg Dekker, IP Services Product Manager for Telia Carrier, says Telia Carrier measured attacks in both quantity and size of attack; the latter is measured in bits and packets.
In addition, the operator noted in its DDoS report that DNS and NTP amplification attacks were the most common attack vectors last year, that threat activity peaks mirrored COVID lockdowns in the spring and fall in US and Europe, and carpet-bombing attacks are on the rise.
"Any amplification attacks are beneficial to the attacker," says Dekker. "They can create a couple of small requests to a certain host that then in terms of volume or the response is significantly larger than any traffic they could generate themselves." Scrubbing legitimate from illegitimate traffic is a real challenge when addressing DNS attacks as false positives can be common, adds Dekker.
According to the report, the mirroring of high-levels of threat activity with COVID lockdowns was likely "largely opportunistic, as cybercriminals took advantage of a sudden shift to remote working and learning. Customers didn't just feel the pain of more attacks but had to deal with more multi-vector attacks to boot – fueling greater reliance on auto-mitigation."
Figure 1: 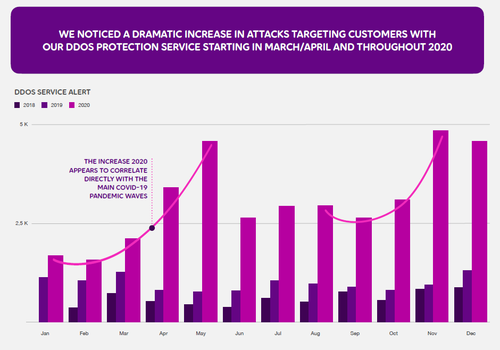 Click here for a larger version of this image. (Source: Telia Carrier.)
Click here for a larger version of this image. (Source: Telia Carrier.)
As enterprises became more reliant on cloud applications and remote systems during the pandemic, bad actors increased extortion-based attacks, says Telia Carrier.
"In some ways there was an increase in attacks … and ransom attacks or ransom demands where people may be put under some relatively small DDoS attacks and then contacted by the perpetrators saying 'if you don't pay X amount of bitcoin, we'll attack you again next week.' Some of those do materialize into bigger attacks and others are opportunistic – people trying to extort some money," says Dekker.
Verizon's recent Data Breach Investigations Report (DBIR) revealed that phishing and ransomware attacks increased by 11% and 6% in 2020, respectively. Hackers are also increasingly working together to share ransomware tools. In a recent podcast with NTT Security executives David Gray and Bruce Snell, Gray explained an emerging trend of ransomware-as-a-service where bad actors work together and sell ransomware and malware to other hackers.
On this episode of the Light Reading podcast, NTT Security's Bruce Snell and David Gray discuss the recent Kaseya ransomware attack, and why bad actors are increasingly targeting the supply chain. Light Reading Podcasts · NTT Security's Bruce Snell and David Gray: Tracking Kaseya
Telia Carrier's Dekker says to thwart hackers, the service provider works with its customers to scrub traffic in real-time and drop anything that's suspicious.
"You can have big fat pipes to the Internet but with the ability of attackers to generate very, very large attacks, they can still fill these pipes and cause you problems. Even if you have a filtering system in your network, it's often best to drop this traffic before it even touches your network," he says.
Dekker adds that Telia Carrier also has a Multihomed DDoS service for customers that purchase IP access from more than one provider. Instead of having to purchase DDoS protection from multiple carriers, Telia Carrier customers can cover their whole network with the Multihomed DDoS service.
— Kelsey Kusterer Ziser, Senior Editor, Light Reading
About the Author(s)
You May Also Like




_International_Software_Products.jpeg?width=300&auto=webp&quality=80&disable=upscale)







