Ethernet
A data-link layer protocol commonly used to transfer Internet Protocol (IP) packets over cables in local area networks (LANs)
August 1, 2001

Before reading this you may find the following tutorials useful:
Protocol Basics, Internet Protocol (IP)
In nineteenth-century physics, the “Ether” was believed to be a weightless, transparent, frictionless, and undetectable substance through which all electromagnetic waves travelled. Early in the twentieth century this concept was scrapped as a bad idea, but the term lives on in a protocol known as “Ethernet.”
The TCP/IP protocol suite prepares packets of data from a computer for their foray into the outside world. It straps on the essential addressing information for the data’s journey, as well as giving error detection and correction capabilities. But IP alone cannot take a data packet out of a computer. This function is usually provided by the data-link layer protocol: Ethernet.
Ethernet is a standard for transmission of information through local area networks (LANs) such as office networks. Every device connected to the LAN has an associated address that is hard-wired to it, in contrast to IP addresses that can be changed through software. This is a six-byte MAC (Medium Access Control) address that will be an inherent feature of any Ethernet card connected to a PC. The Ethernet protocol adds its own framing structure to the IP packets, with a header size of up to 26 bytes. The Ethernet frame structure contains the source and destination MAC addresses, as well as control and additional error-checking functionality if required. The minimum data payload size in the Ethernet frame is 46 bytes, with a maximum of 1500 bytes.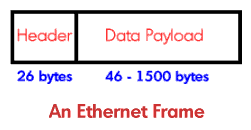 Ethernet now provides access to the physical medium through which the data must travel – the cable connected to the PC. This is achieved through a method known as Carrier Sense Multiple Access/Collision Detection (CSMA/CD). This technique works a lot like crossing the road. You approach the curb and look to see if there is any traffic in the road. In this case, the Ethernet card takes a look out onto the cable and senses any activity in the form of traffic from other PCs on the link. If it senses traffic on the cable, then it waits a set time before looking again. Just as if you see a large truck coming along you will, ideally, wait before trying to cross.
Ethernet now provides access to the physical medium through which the data must travel – the cable connected to the PC. This is achieved through a method known as Carrier Sense Multiple Access/Collision Detection (CSMA/CD). This technique works a lot like crossing the road. You approach the curb and look to see if there is any traffic in the road. In this case, the Ethernet card takes a look out onto the cable and senses any activity in the form of traffic from other PCs on the link. If it senses traffic on the cable, then it waits a set time before looking again. Just as if you see a large truck coming along you will, ideally, wait before trying to cross.
Once the Ethernet card detects no activity on the link, it begins to send out its own Ethernet frames in the form of electrical 1s and 0s. However, there is the chance that another device has also looked at a similar time and sent out its own Ethernet frames. In this case there is a collision and no data gets through. Ethernet is designed to detect this and therefore has the ability to retransmit the information again when it will hope to have more success.
With many PCs all connected via the same cable, the likelihood of collision is so high that it’s surprising any information ever gets transferred at all. It is indeed these collisions that limit the possible length of cable in a system, as greater lengths of cable provide more scope for devices to transmit at similar times without detecting activity on the link. A technology known as switched Ethernet aims to improve matters by dividing links into separate sections, thus reducing the number of devices with access to one particular section and so reducing collisions.
The destination MAC address in the Ethernet frame takes it onto the nearest IP router, which strips off the Ethernet header to handle the raw IP packet. Once the router has decided where to send the packet next, towards its IP destination address, it is again framed by Ethernet and retransmitted using CSMA/CD once more.
Ethernet comes in a variety of flavors. The most often encountered is known as 10Base-T, which has a 10-Mbit/s transfer rate and uses unshielded twisted pair (UTP) cable as its access medium. The length limit on such a system is around 100 meters. 100Base-T is often known as “fast Ethernet” and gives 100-Mbit/s transfer speeds, again on UTP cable with an upper length limit of 100m. The most modern flavor is “gigabit Ethernet,” which provides 1-Gbit/s access rates on optical fiber over distances up to several kilometers.
Key Points
Takes IP packets out into the network
Uses Medium Access Control (MAC) addresses for devices
Ethernet frame carries data along with source and destination MAC addresses and error-checking information
Accesses unshielded twisted pair (UTP) cable by sensing activity and only transmitting if nobody else on the cable is doing so
Collisions can limit the range of Ethernet networks
Fast Ethernet gives speeds of up to 100 Mbit/s over distances up to 100m
Gigabit Ethernet can transmit on optical fiber over distances of several kilometers
Further Reading
Formatting for Transmission, Sonet (Synchronous Optical NETwork) and SDH (Synchronous Digital Hierarchy)
You May Also Like


_International_Software_Products.jpeg?width=300&auto=webp&quality=80&disable=upscale)







