Pretexting outpaces phishing, reports Verizon DBIR
Since even hackers like an 'easy button,' pretexting constituted 50% of all social engineering attacks, a rate that doubled since the previous year, according to Verizon Business' 2023 Data Breach Investigations Report.

Hackers must be fans of MTV's show Catfish with the amount of pretexting they've been engaged in recently. While catfishing is often equated with luring a potential romantic partner, pretexting usually involves deploying a fake persona with the goal of financial gain.
Since even hackers like an "easy button," pretexting constituted 50% of all social engineering attacks, a rate that doubled since the previous year,* according to an annual security report by Verizon.
Authors of Verizon Business' 2023 Data Breach Investigations Report analyzed 16,312 security incidents and 5,199 breaches, which occur when a bad actor successfully exfiltrates data from an organization. A distributed denial of service (DDoS) attack would be considered an incident instead of a breach since data wasn't leaked to an unauthorized party.
Of those 5,199 breaches, nearly three out of every four (74%) involved a human element, which includes social engineering attacks, errors, misuse of credentials, clicking on a link in a phishing email and more.
Pretexting overtakes phishing
Taking a closer look at the rise of pretexting, Alex Pinto, one of the lead authors of the DBIR, told Light Reading it occurs when bad actors create a scenario and false persona to trick a victim into sharing private information. Pretexting is popular among hackers because it's easy to deploy and there's a "low barrier to entry," he explained.
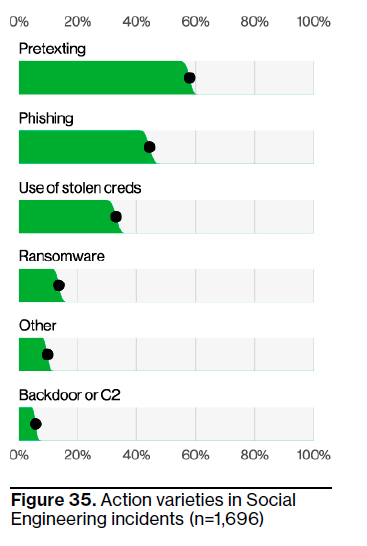
Phishing accounts for 44% of social engineering attacks versus 50% due to pretexting.
(Source: Verizon Business DBIR)
"The thing that really brought it to our attention, is that it overtook phishing as kind of the main factor among social engineering attacks," said Pinto. While phishing is still prevalent, it accounts for 44% of social engineering attacks versus 50% due to pretexting.
A common example of pretexting is business email compromise (BEC), which increased over the past few years as well. The median amount stolen in BECs is $50,000, based on Internet Crime Complaint Center (IC3) data.
Bad actors varied their approaches to sneaking into organizations by using stolen credentials (49%), phishing attacks (12%) and exploiting vulnerabilities (5%). Money was the main motivator – 3% of hackers were motivated by espionage while the remaining 97% were driven by financial gain.
Ransomware becomes more expensive
Ransomware continues to be a popular choice by hackers, amounting to one in four breaches. The cost per ransomware incident has doubled over the past two years to $26,000. Ransomware is malicious software (malware) that encrypts an organization's data; bad actors demand a high fee to restore access to the data and in many cases, prevent distribution/exposure of that data.
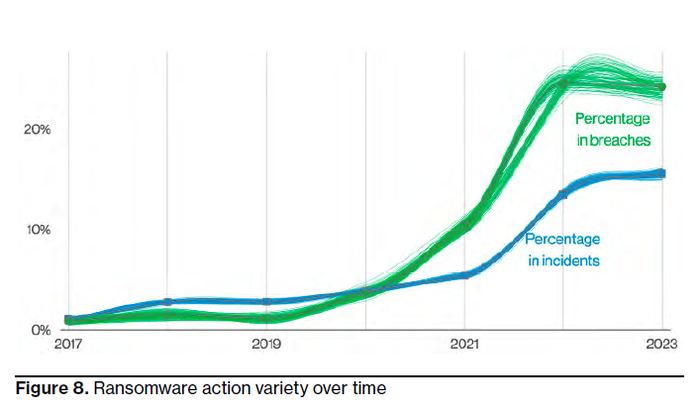
"While it did not actually grow, [ransomware] did hold statistically steady at 24%," said Verizon.
(Source: Verizon Business DBIR)
"Things like BEC and ransomware tend to continue growing and capture a large market share of potential attacks because they're easy, low cost or very efficient," said Pinto.
For 95% of ransomware incidents that resulted in a loss, it cost an organization anywhere from $1 to $2.25 million.
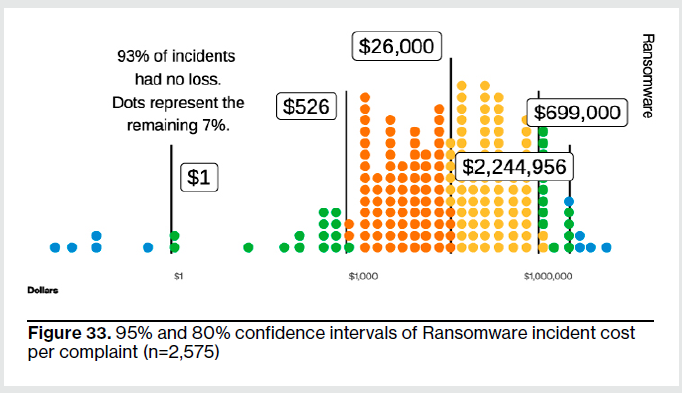
For 95% of ransomware incidents that resulted in a loss, it cost an organization anywhere from $1 to $2.25 million.
(Source: Verizon Business DBIR)
"This rise in cost coincides with a dramatic rise in frequency over the past couple of years when the number of ransomware attacks was greater than the previous five years combined," said Verizon. Ransomware continues to be one of the top cyberattack methods and accounts for 24% of all breaches.
Pinto said ransomware's popularity likely stems from being "good at converting a breach into money," and even the smallest companies are often willing to pay the ransomware fee to protect their data.
Log4j vulnerability
Verizon's DBIR also took a look back at the Log4j vulnerability, which was initially disclosed in late November 2021. More than 32% of all Log4j vulnerability scanning for the year* occurred in the first 30 days after its release. Fortunately, Pinto said, a strong initial response to the threat resulted in avoiding a "huge disaster."
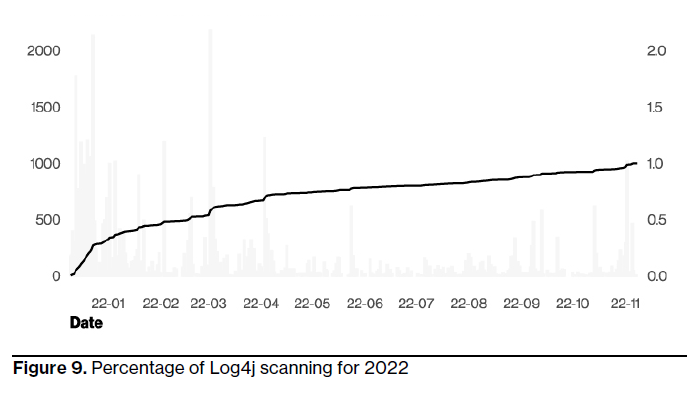
(Source: Verizon Business DBIR)
"There was swift action from the community to spread awareness and patch all the different systems that had Log4j as a component," according to Verizon's DBIR. "That surely helped avert a bigger disaster, so our success makes it look like it wasn't a big deal after all."
Don't be scared
The myriad ways hackers can threaten an organization can be scary, especially for small and medium-sized businesses (SMBs), but Verizon suggests that enterprises can protect their data "through the adoption and adherence of industry leading protocols and practices."
The DBIR also includes specific recommendations for SMBs, explaining where to start on their journey to better securing their infrastructure, such as utilizing the CIS Critical Security Controls Navigator to adopt security standards.
Verizon also recently joined the Mutually Agreed Norms for Routing Security (MANRS), a global initiative to provide fixes to "reduce the most common routing threats that can be exploited by attackers."
*Editor's Note: Verizon's DBIR covers the period from Nov. 1, 2021 to Oct. 31, 2022 and is in its 16th year of publication.
Related posts:
— Kelsey Kusterer Ziser, Senior Editor, Light Reading
About the Author(s)
You May Also Like












