Forms of communication among network devices to enable the exchange of information
August 1, 2001

Before reading this you may find the following tutorials useful:
Optical Networks, Optical Fiber, Ethernet
We encounter protocols all the time in our everyday lives. There are very specific ways in which we need to communicate to achieve certain goals, and doing so entails the use of protocols. Confessing your indiscretions to your priest, confiding them to your bartender, or committing them with your landlord's wife – each interaction demands a different approach. Each calls for the use of a different protocol.
A network consists of devices that – to anthropomorph them – wish to exchange information. They use “network protocols” as a way of talking to each other in order to achieve their own individual goals. By merely clicking on the link to this Web page you initiated numerous protocols that rapidly triggered different functions within different devices, until the information that you requested was brought gloriously up on your screen.
Certain tasks are suited to communicating in bursts, and for such information traveling through a network it is usually sensible to use some form of “packet-switching” protocol. This is, in fact, how this Web page interaction we are having is taking place. As we do not require constant communication while you are reading this, there is no need for our computers to be talking with each other. Once you request another page from this site, your click will create a “packet” of information requesting the page, and the page will then be sent to you in the form of several packets that your computer will cleverly piece together. The packet switching protocol will handle this splitting of information, control its travel through the network, and then make sure that it is pieced together correctly at the end.
A voice conversation between two people on standard telephones requires a constant connection to be in place – in the form of what is known as a “circuit.” Once two people are in conversation, a circuit-switching protocol has initiated a constant connection between them, continually carrying any sounds that are made. Even if there is silence, the circuit is still in place and transmitting that silence.
Networks would be simple things if there were just one protocol to follow when communicating between devices. However, you will be pleased to know that there are several individual layers of protocols, which all combine to transport data around a network. In describing how this Web page reached you, let us look at the journey through this protocol “stack,” which is known as the Open Systems Interconnection (OSI) model.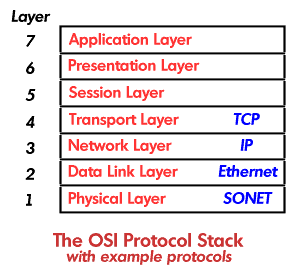 It all started on your computer in the top layer of the stack – the application layer. This is provided by your Web browser, which presented you with a link to this very tutorial. Being the shrewd and accurate judge of quality that you are, you gave it a click. This request was then passed on to the presentation layer, probably also contained within your browser, which translated your click into a piece of data that will ultimately be understood at the Light Reading Web server as a request for this page.
It all started on your computer in the top layer of the stack – the application layer. This is provided by your Web browser, which presented you with a link to this very tutorial. Being the shrewd and accurate judge of quality that you are, you gave it a click. This request was then passed on to the presentation layer, probably also contained within your browser, which translated your click into a piece of data that will ultimately be understood at the Light Reading Web server as a request for this page.
The session layer is used to initiate communication between our two machines and maintain it while we are having our brief exchange. Your request is then passed down to the transport layer, which controls the overall integrity of the connection that will be established between your PC and the Web server. Transport Control Protocol – TCP – is usually used at this stage. It basically works to ensure that your message will reach the Web sever, retransmitting it if it is lost, correcting any errors, and making sure it is in the correct order. In the network layer, layer 3, your request is now bundled up into a packet, probably formed by Internet Protocol – IP. This attaches addressing information to help routers in the network to direct your data to the correct location.
Both TCP and IP facilities are provided in your computer, as well as some data-link layer protocol such as Ethernet which will then put your packet of information into a “frame.” This framing is your packet's ticket out into the wide world, allowing it to flow out from the wire connecting your computer to the network. It also gives some error-detecting capabilities to make sure the frames received at the other end of the wire are exactly as they were when they left your machine.
The Ethernet frames will travel to some central point at which further framing (perhaps provided by a protocol called Synchronous Optical NETwork - Sonet), surrounds them in the physical layer. This gives your data a ride out into the wonderful world of optical fiber where it can then travel the bulk of the distance between our two locations. The additional Sonet framing is needed to track the signal's integrity through the optical fiber, and monitor the status of the fiber connection, maybe providing rerouting if a link is unavailable.
Your request then completes its optical journey much closer to the location of the Web server. The process of traveling back up the layers of the OSI stack will now begin. The Sonet framing will be stripped off at the end of the optical fiber section of the link, and eventually a raw IP packet will reach the Light Reading Web server. The IP packet will then be stripped down to your initial Website request that was formed so many milliseconds ago at your Web browser. Once this is interpreted, the Web page can be sent, and the data you requested is again packaged up all the way down the OSI stack, for you to receive it at the bottom and again strip it down to get the Web page displayed on your browser.
It should be noted that modern systems are designed to remove and integrate as many of these protocol layers as possible in an attempt to introduce simplicity into the network. This is a shame if you enjoy a good strip show, but probably a sensible idea for the people who have to control these networks.
Key Points
Protocols are used by network devices for communication
Sporadic data exchanges, such as Web traffic, are best served by packets
Continuous information streams, such as phone calls, are better suited to circuits
The seven layers of the Open Systems Interconnection (OSI) model provide a framework for protocols
Attempts to simplify overall network designs may include some integration of layers
Further Reading
Internet Protocol (IP), Formatting for Transmission
You May Also Like









